Add server-side encryption
Server-side encryption (SSE) in Amazon S3 automatically encrypts data when it is written to the storage service and decrypts it when accessed, providing robust data protection, compliance with regulatory requirements, and ease of management.
Server-side encryption with Amazon S3 managed keys (SSE-S3) is free. Other encryption options may incur costs. Amazon offers pricing details on their pricing page.
What we'll be doing
- Review the existing module
- Configure server-side encryption (SSE)
Review the existing module
Start by cloning the Nitric repository, then examine how the Terrraform provider provisions an S3 bucket.
git clone https://github.com/nitrictech/nitriccd nitric
The AWS S3 module in the default Terraform provider performs the following tasks:
- Creates a unique ID for the S3 bucket to ensure unique naming.
- Provisions an S3 bucket with a unique name using the generated ID.
- Tags the bucket for identification.
- Grants S3 permission to invoke specified Lambda functions.
- Configures S3 bucket notifications to trigger Lambda functions based on specified events using dynamic blocks.
To begin our customization, we will start adding configuration to this module.
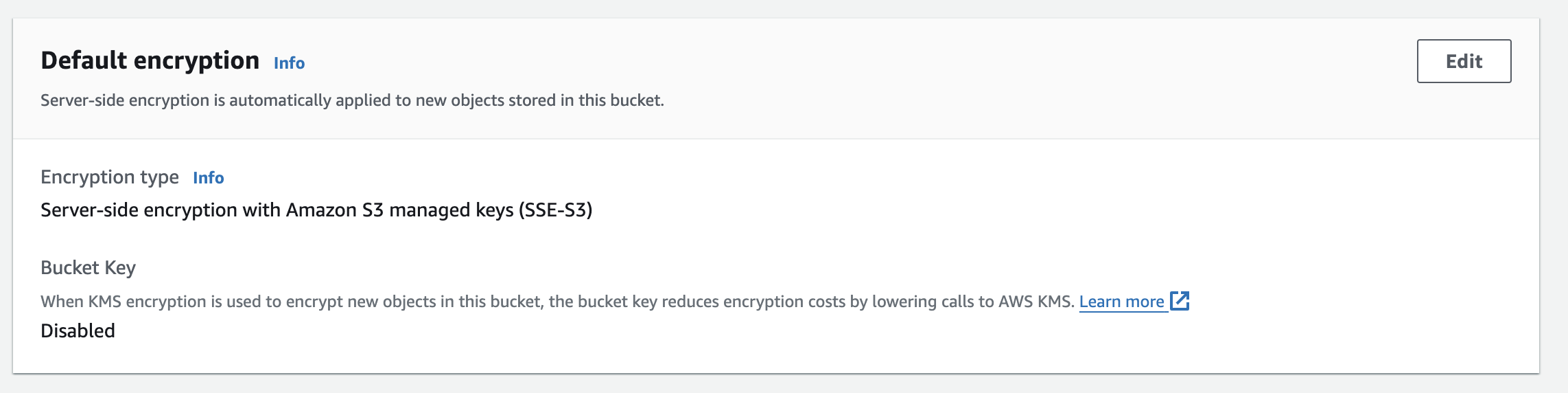
Add server-side encryption (SSE)
Add the following at the end of aws/deploytf/.nitric/modules/bucket/main.tf:
# AWS S3 bucket server-side encryption configurationresource "aws_s3_bucket_server_side_encryption_configuration" "bucket_encryption" {bucket = aws_s3_bucket.bucket.bucketrule {apply_server_side_encryption_by_default {sse_algorithm = "AES256"}}}
Full documentation can be found on the Terraform registry.
Build and use your modified provider
The Nitric project includes a make file that will build and install your provider as nitric/awstf@0.0.1 by default.
Navigate to nitric/cloud/aws and run make install to build and install the modified provider binary.
cd nitric/cloud/awsmake install
The provider can then be used directly in your project's stack file as follows.
# The nitric provider to useprovider: nitric/awstf@0.0.1# The target aws region to deploy toregion: us-east-2
If you don't have a stack file use nitric stack new to create one.
You can generate the Terraform project as usual by running the nitric up command:
nitric up
To deploy the application using Terraform, you can navigate into your Terraform stack directory and use the standard Terraform commands:
terraform initterraform planterraform apply
Finally, log into the AWS console to verify the encryption configuration was applied.
Have feedback on this page?
Open GitHub Issue